How to safeguard your computer from fraudulent Windows Defender Security Center notifications
Identifying and Responding to Technology Support Frauds
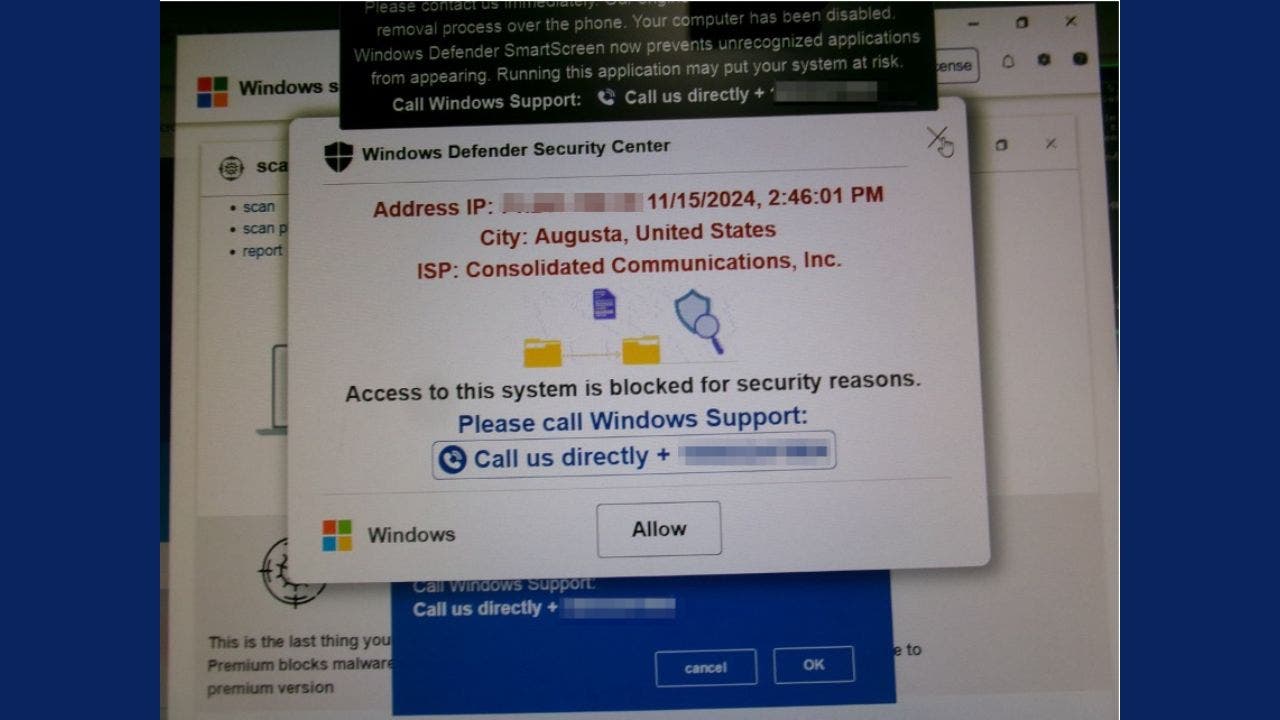
Janet D. described her recent unsettling experience in an email she shared with us.
"Windows Defender Security Center displayed a pop-up message on my computer, which read 'Access to this system is blocked for security reasons,' and included an audio message and siren."
In a panic-inducing situation, Janet followed the instructions of many and called the number displayed on her screen. She was instructed to press Ctrl + Shift + Esc to unfreeze her computer, but the scammer's instructions didn't stop there. He directed her to download software from UltraViewer.net, a legitimate remote access tool often exploited by bad actors. If you ever encounter a similar scam, here's what you should know.

3 red flags to recognize a tech support scam
Pop-ups claiming to be from Microsoft or other security services are often fake alerts that masquerade as official warnings. Legitimate companies do not issue pop-ups with support numbers or direct you to download remote access software.
Scammers use sirens, flashing messages, and dire consequences to create a sense of urgency and push victims into immediate action without critical thinking.
Scammers frequently use software like UltraViewer, TeamViewer, or AnyDesk to infiltrate victims' systems. Although these tools are useful for remote technical assistance, downloading them at the request of an unknown individual is a warning sign.

Steps to take if you encounter a scam like this
If you encounter a scam, promptly take the necessary steps to safeguard yourself and your data.
Don’t engage
If you receive a suspicious pop-up, do not click on any links or follow any instructions. Instead, research the phone number or message independently. Use Ctrl + Alt + Del to open the Task Manager and close the browser or application displaying the message.
Assess potential damage
Scammers exploit pressure. Pause and evaluate the circumstances. Janet inquired about the scammers obtaining any data. Here's the action plan.
- After the incident, remove any unknown software that was installed.
- Check your email, banking, and other important accounts for unauthorized sign-ins or transactions.
- To ensure your devices are protected from malicious links, malware, phishing emails, and ransomware scams, it is recommended to install antivirus software on all your devices. For the best 2024 antivirus protection winners for Windows, Mac, Android, and iOS devices, get my recommendations.
Secure your system
If you have UltraViewer or similar tools installed, remove them promptly. Update passwords for essential accounts, prioritizing email and banking logins. Utilize a password manager to create and store complex passwords. Activate two-factor authentication to enhance security even if someone gains access to your login information.
Seek professional help
If you suspect that your computer is still compromised, it might be best to seek professional help to ensure your system is secure. You may want to contact Microsoft Support for additional guidance and to report the incident to help prevent others from falling victim.

Why Janet didn’t receive a warning from her antivirus software
Janet pointed out that her antivirus software did not detect the scam. Unfortunately, many scams use social engineering instead of malware to evade detection by antivirus software. These scams exploit human psychology, not just technical vulnerabilities. Nevertheless, conducting regular scans can still help identify hidden threats.
What do I do if I provided personal information to a scammer?
Don't be embarrassed if it happens to you, as it could happen to anyone. The worst thing you can do is stay silent. You can help prevent it from happening to others.
Immediately stop all communication with the scammer. Do not engage further or respond to any messages or calls from them.
Notify your local law enforcement agency or the cybercrime unit in your country about the scam and provide them with all the details you have about the scammer and your communication with them.
Contact your bank and credit card companies immediately if you shared any financial information. Inform them about the potential scam and seek advice on securing your accounts.
Keep a vigilant eye on your financial accounts, including your bank accounts, credit cards, and any other financial accounts, for any suspicious activity. Immediately report any unauthorized transactions.
Contact credit reporting agencies to place a fraud alert on your credit report, which can prevent fraudsters from opening new accounts under your name.
Be cautious about future communications from unknown sources, as scammers may try to target you again using different tactics.
Consider subscribing to an identity theft service that includes identity theft insurance of up to $1 million and a white-glove fraud resolution team to help you recover any losses if a scammer gets a hold of your personal information.
Kurt's key takeaways
Be cautious of scams that exploit fear and urgency, even if you are vigilant. Recognizing red flags such as unsolicited pop-ups, high-pressure tactics, and requests for remote access can help protect your personal information. If you encounter a situation like Janet's, stay calm, verify the legitimacy of any alerts, and take the necessary steps to secure your system. Scammers rely on quick reactions, so slow down, stay in control, and don't let them manipulate your next move.
Please inform us at Cyberguy.com/Contact if you have encountered any new scams recently that others should be aware of.
To receive my tech tips and security alerts, sign up for my free CyberGuy Report Newsletter at Cyberguy.com/Newsletter.
Follow Kurt on his social channels:
Answers to the most asked CyberGuy questions:
New from Kurt:
- Kurt's Holiday Deals extended
Copyright 2024 CyberGuy.com. All rights reserved.
tech

15 things to do or try first when you get a new iPhone: 1. Set up your phone with your personal information and preferences. 2. Install your favorite apps and games. 3. Connect your phone to your Wi-Fi network and other devices. 4. Take a few photos and test out the camera. 5. Set up your email and other accounts. 6. Enable security features like Touch ID or Face ID. 7. Customize your phone's settings and appearance. 8. Explore the built-in features and apps on your phone. 9. Connect with friends and family on social media. 10. Set up reminders and alarms. 11. Use the phone's built-in voice assistant. 12. Download and install new apps from the App Store. 13. Set up your phone's screen time and parental controls. 14. Enable automatic updates for your apps and software. 15. Back up your important data to cloud storage or an external hard drive.
techYou might also like
- Your credit score could be negatively impacted by these mistakes.
- How to repurpose your old iPhone for a new purpose
- The world is privy to the robot training techniques of a Chinese tech company.
- An early supernova was captured in photos by a powerful Webb Telescope.
- If you suspect your computer is infected with a virus, take action immediately.


















